Internet Protocol (IP) addresses are how the Internet keeps track of who is where. They aren’t necessarily attached to specific email addresses, but they do contain potentially valuable information about a person’s geographic location (although, as we’ll see, this is an imperfect science). It stands to reason that the more information you know about your subscribers, the easier it is to tailor your content to fit their interests, so there is some value in attaching IP information to each email address, but be careful: Where you and your customers reside can affect the legality of this practice.
Using the IP Address
Your computer’s IP address is like a landline telephone. If everyone in a household is using that telephone, then everyone will show up under the same number. Like a telephone number, an IP address can give you a good idea as to where someone is located without showing you the exact address. A search on our own IP, for instance, turns in different results, but they are all in the Bay Area, which is where our headquarters are located. Even with this limitation, an IP address will narrow down the possible location of the subscriber, which can, in turn, help greatly with certain types of marketing.
Dynamic vs. Static
There are two kinds of IP addresses—dynamic and static. Their names suggest exactly what they are. A static IP address is one that never changes. Companies, for instance, will often be use a static IP address to help them send and receive data and allow others to easily log onto their servers. A static IP address is mandatory for certain activities such as VoIP and VPN to ensure stable connections. Individuals might also opt for static addresses if they plan to host a website on a server, or are highly active in the online gaming community.
Dynamic IP addresses are often used for home connections. They are considerably cheaper and the end user doesn’t have to worry about network configuration since this is handled automatically. As one might expect, geolocation is a little more reliable with a static address than a dynamic one, although both have some value here.
Linking IP addresses to the email addresses gives you ability to provide information as to when and where a person opted to receive email from you, eliminating potential claims that your mailings were unsolicited. Some ISPs ask for this information when investigating spam complaints. But there is a big caveat to using this approach: It might be against the law.
IP Addresses and the Law
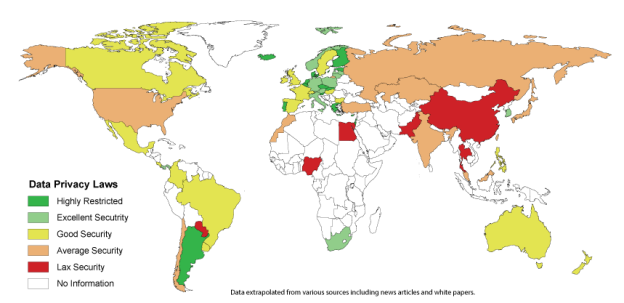
The legality of linking IP addresses to email addresses changes from country to to country. In some countries, it is perfectly legal, while others see it as a violation of privacy, allowing it only after the subscriber has agreed to let the ESP use that information. In the US, for instance, there is no single, comprehensive federal law regulating the collection and use of personal data. Even if there were, the odds of it being enforced are slim considering that the FTC only brings a handful of cases against emailers to court every year, and most of those are because the products these companies are selling don’t work, rather than privacy breaches or CAN-SPAM violation.
In Canada, which has some of the strictest spam laws on the books, a record of an opt-in is required. Canada has strict rules about what information the government can gather about a person, but the laws concerning the private sector appear less well defined. If businesses aren’t allowed to attach IP information to email addresses, then the verification of subscription becomes a lot harder. This summer, a second aspect of CASL takes effect that lets individuals challenge a company’s email programs, meaning anyone can bring any company to court. This sounds like a recipe for disaster, but only time will tell.
In Great Britain, you can collect IP addresses, but you start treading into the danger zone once you connect those IP addresses to individual email accounts. An IP address by itself isn’t considered personal data, but when it’s combined with other information to build a profile of an individual, it suddenly becomes personal data—even if that individual’s name is unknown. You’ll need to get permission from the recipients to do so. This isn’t a big deal., although most British companies use these additional requests for more specific information, such as the location of the recipient’s preferred store.
In most of the rest of Europe, things get even even trickier. In Europe, static IP addresses have been considered personal data for some time now, but on October 19, 2016, the Court of Justice of the European Union (CJEU) ruled that dynamic IP addresses can also qualify as personal data under EU privacy law. Additionally, the Swedish Supreme Administrative Court has ruled that collecting and storing IP addresses is in violation of the Personal Data Act.
These laws have been further enforced with the approval of the EU General Data Protection Regulation (GDPR). The regulation was passed by the EU Parliament in April of 2016. Although not specific to email, the regulation does require businesses to keep tight controls on their private data and gives your subscribers the “right to be forgotten.” Any data you have on them needs their approval and they can nix it at any point. This includes their name, photos, email addresses, bank details, posts on social networking websites, medical information, and computer IP addresses. The regulation has a two year grace period before they start cracking down on violators, and applies to any business doing business in the European Union.
The irony here is that by not allowing the ESPs to use this information, it makes it harder to verify when someone not associated with that email address is pranking the actual addressee, making it far more likely for that person to receive spam than they otherwise would.
Over in China they have a completely different take on the matter. As far as they’re concerned, an IP address in isolation isn’t personal data because it’s focused on a computer and not an individual. This reasoning was applied by the Hong Kong Privacy Commissioner in a complaint about Yahoo!’s disclosure of information about a journalist to Chinese authorities.
Approach With Caution
So what is the best technique? If your company does no business outside of the United States, and never plans to expand past that country’s borders, IP collection isn’t an issue. If, on the other hand, your clientele is international and you need to stay compliant in several countries, you’re better off either forgetting about collecting IP information, or adding a check box to the sign-in process to verify that the recipient has approved your use of their IP address information. Given the constantly shifting landscapes or laws on this subject. Some type of verification from the users that it’s okay to note their IP addresses is the safest route.